8MAN
Access Rights Management

8MAN is the leading solution for Access Rights Management (ARM) in Microsoft and virtual server environments (AD). It protects the business from unauthorised access to sensitive data. The software solution developed in Germany by Protected Networks sets the benchmark for professional network security and agile IT organisation. It bundles state-of-the-art functionality with the fulfilment of current security and compliance guidelines. The core functions of 8MAN include: Permission Analysis, Security Monitoring, Documentation & Reporting, Role & Process Optimisation and User Provisioning
Solution for Access Rights Management with 8MAN
- Intelligent full-text search
- Historical data
- Delegation
- Web-based approval process
- Multi-user operation
- For locations distributed around the world
PERMISSION ANALYSIS
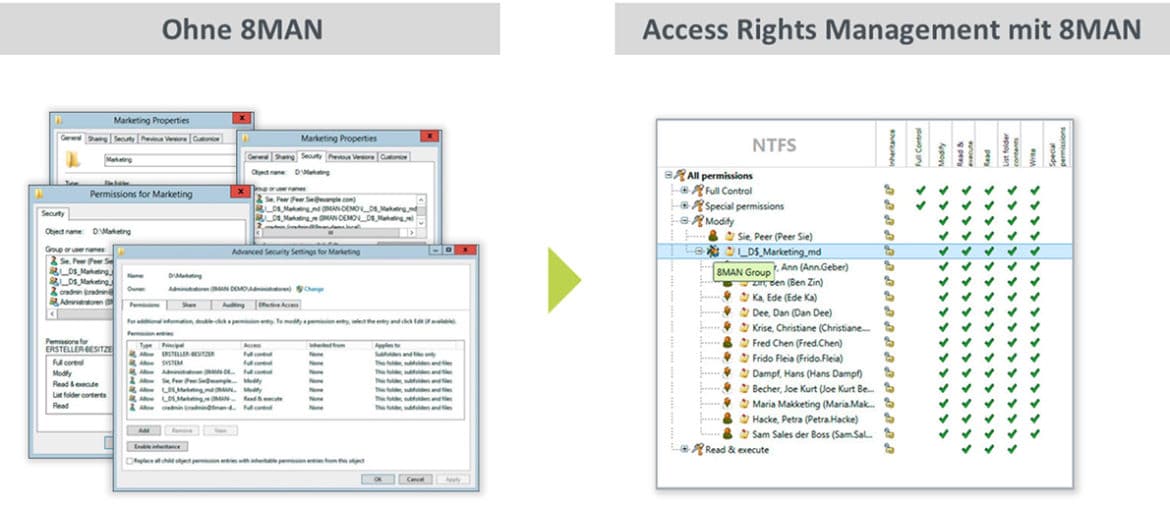
If you cannot see the danger, it is hard to fight it. 8MAN analyses the authorisation situation in your business and shows you who can access which resources. From a central viewpoint, you can see the group memberships from the Active Directory and the access rights for your file server, SharePoint Sites, Exchange, Office 365 or any other SQL Database. Now that you have this information you will know what to do and be able to protect your company from internal breaches of security.
8MAN gives the control back to you. Just one click on the resources view and you can see the current status of a scanned system and the employees who are authorised to be there.
DOCUMENTATION & REPORTING
8MAN creates reports that are vital. Auditors are astounded when they see the access rights of an employee. Managers are relieved to know who has access to the personnel data folder. The reports can be configured with just a few clicks, so everyone can understand them and they can be sent out automatically. A report is drawn up in two steps: Defining the resources to be analysed and selecting the output format.
SECURITY MONITORING
A whole number of employees make changes in the Active Directory as well as on the file server. Without a fully comprehensive monitoring system there will inevitably be risks to the security. With the 8MATE AD Logga (for the Active Directory) and the 8MATE FS Logga (for file servers), you can record all the security-related activities in your company’s network. This will help you to understand who has done what in the network and to clarify the causes in the event of problems. At the process level, you will gain complete transparency of the Access Rights activities. Even changes made outside of 8MAN are recorded. You can optimise your Access Rights Management process on the basis of the information you have gained.
ROLE & PROCESS OPTIMIZATION
It is not just the administrator who knows best regarding who should have access to what, but also the respective data owner and the supervisor. By introducing a role concept for analysing and granting access rights, you are contributing to increased data awareness and the appropriate action in your company. More specifically, you are creating an organisational chart of your company and including all the departments. Next you will show the individual data owners to your employees. The data owners analyse or assign the access rights of your employees to the resources. With the 8MATE GrantMA add-on module, the employee can order new authorisation via a web portal. The data owner then decides whether to approve the request in a user-defined workflow.
USER PROVISIONING
Create new users in a matter of seconds with role-based templates. The process for generating users is standardised and designed according to the roles in your company. The group access rights defined in the Active Directory for the file server, SharePoint Sites, Exchange and virtual servers are assigned at the same time.
So that the new employee can get started right away, 8MAN generates the corresponding e-mail account. Schedule the activation to prepare for an entry in the future or to limit time involved in project work. Whether it is the Helpdesk or data owner: In both cases, those involved work with a reduced, simple interface. All accesses are set up in just a few steps.