Privileged Account Management
Privileged user accounts – identify, protect, monitor and manage

CyberArk is the only vendor of security solutions that focuses specifically on the fight against targeted cyber threats, on – undetected – attacks that penetrate right into the heart of the company. More than 3,075 companies around the world have placed their faith in CyberArk to protect their valuable data, and out solutions can fulfil all the requirements of audit and IT compliance.
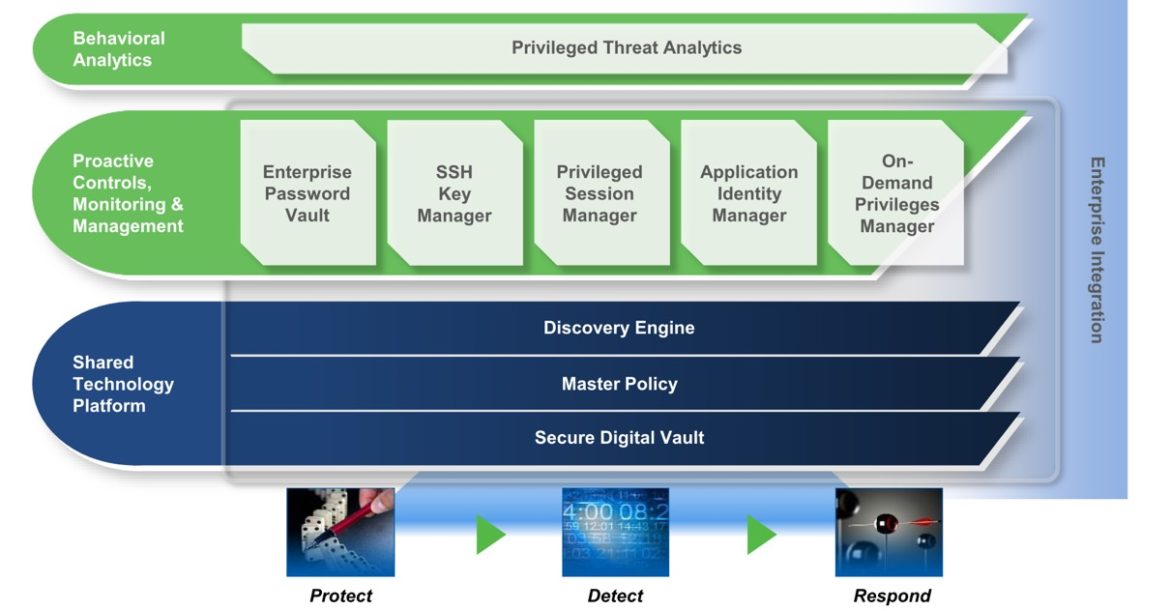
Privileged Identity Management™ (PIM) solutions are used to securely manage, automatically change and to monitor all the activities relating to privileged user accounts. Secure privileges user accounts and administration passwords in routers, servers, databases, workplace computers and applications. Create a centralised location to maximise your security, simplify the updates, optimise system maintenance and to comply with the regulations and the recommended security procedures for all types of privileged accounts.
CyberArk is your reliable expert when it comes to the security of privileged accounts. CyberArk has developed a high-performance modular technology platform from scratch that is completely focused on security and provides the industry’s most comprehensive security solution for Privileged Accounts. Each product can be independently managed or combined with a connected end-to-end solution for operating systems, databases, applications, hypervisors, network devices, security applications and many more application scenarios. The solution was designed for On-Premise-, Hybrid-Cloud and OT-/SCADA environments.
Answers to the questions of who, when, why and what
The CyberArk security solution for Privileged Accounts is based on the CyberArk Shared Technology Platform™, which consists of a Vault Server, a uniform Policy Engine and a Discovery Engine, and it provides scalability, reliability and unparalleled security for privileged accounts.
Advantages of the integrated solution
- Simple, cost-effective preparation of audit reports from a central repository of all the audit data
- Automated enforcement of privileged account policies for continuous monitoring and compliance with the audit requirements
- Complete transparency with respect to all activities in privileged sessions
- Greater convenience for privileged users thanks to the one-off entry of privileged passwords of login credentials
- Lower operating costs due to the central management with a single platform